EagleMsgSpy - Functionality & Infrastructure
EagleMsgSpy Part 2: Functionality
In the last post, we did some initial metadata triage. In part 2, we are going to dig into what this thing is and how it works - The Lookout team already highlighted the key features, but for those looking at these samples in the future, I’m going to save you some work by highlighting where in code these things occur.
After looking at all the samples shared by Lookout, I have a pretty good idea of how this thing works - granted, there are changes between the samples due to this family being developed since at least 2017.
In addition to some broad functionality highlights and interesting strings, I am going to dig into some infrastructure pivoting based on IPs and domains shared by Lookout, as well as some I found that aren’t on the blog.
BLUF
What did we learn:
The samples shared by Lookout cover at least 3 different variants of the MM / EagleMsgSpy family
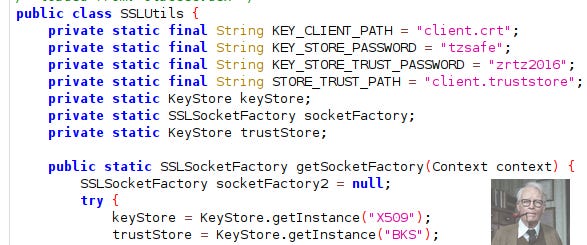
1st iteration used had little to no obfuscation and used multiple tzsafe strings and even a tzsafe crt complete with password
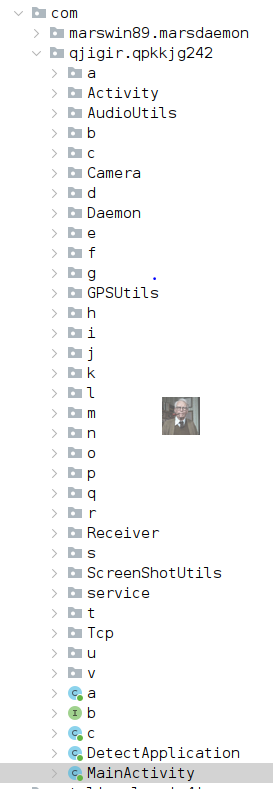
2nd iteration used marsdaemon + multi obfuscation mechanisms & denoted service implementations in code with the “=eagle_” string
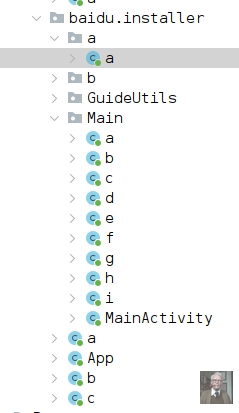
3rd iteration got rid of eagle strings entirely while maintaining MM UI and strings + switched to new GuideUtils structure
I was able to find 7 additional IPs not mentioned on the blog
Found a phone number that I believe (might?) belong to the original developer or one of the original targets
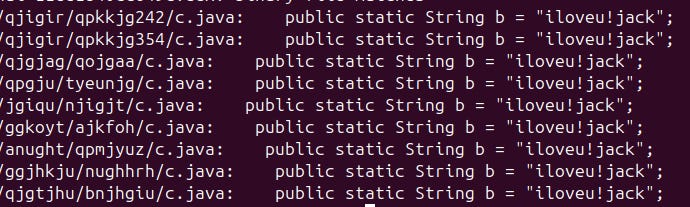
Learned that the original developer does indeed love someone named Jack…at least in 9 of the samples we analyzed
Example flow
(com.baidu.installer) —> (detect.apk) —> decrypted (classes2.dex)
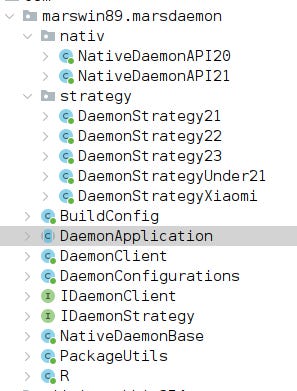
Earlier versions of this family were using com.marswin89.marsdaemon for receivers and keep alive duties:
An overview of this version is displayed below (version: 3.2.8.20200527)
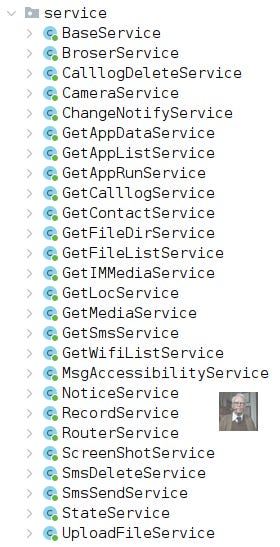
The eagle string makes it easier to see which sections of code implement a given service (thanks developer). This is consistent in 9 of the 17 samples, which I believe are earlier versions of the family. Won’t really go to much into these services, as the names pretty much speak for themselves.
=eagle_access
service.MsgAccessibilityService.java
service.NoticeService.java
*/l/a/a.java
*/l/a/c.java
=eagle_app
service.GetAppDataService
=eagle_base
service/GetMediaService.java
service/GetWifiListService.java
service/GetSmsService.java
service/GetFileListService.java
service/GetAppListService.java
service/GetAppRunService.java
service/GetCalllogService.java
service/GetContactService.java
=eagle_calllog
service/CalllogDeleteService.java
=eagle_camera
*/Camera/a.java
service/CameraService.java
=eagle_change
service/ChangeNotifyService.java
=eagle_java
*/e/g.java
*/f/a/d.java
service/RouterService.java
=eagle_loc
service/GetLocService.java
=eagle_media
*/k/a.java
=eagle_mm
Activity/ScreenShotActivity.java
*/d/a.java
*/e/e.java
*/e/f.java
*/e/a/a.java
*/c/a.java
*/c/b/a.java
*/c/c/a.java
*/c/c.java
*/c/a/a.java
*/a/d.java
*/d/a.java
MainActivity.java
DetectApplication.java
service/MsgAccessibilityService.java
service/NoticeService.java
service/StateService.java
Receiver/PhoneBroadcastReceiver.java
Activity/ScreenShotActivity.java
=eagle_net
*/u/a.java
=eagle_rec
*/p/a.java
*/p/b/a.java
*/p/c/a.java
*/p/a/a.java
*/b/a.java
*/c/b.java
*/c/b/a.java
service/RecordService.java
Receiver/PhoneBroadcastReceiver.java
=eagle_router
service/UploadFileService.java
service/BaseService.java
service/RouterService.java
service/BroserService.java
*/f/g.java
*/a/d.java
=eagle_screen
ScreenShotUtils/ScreenShotActivity.java
service/ScreenShotService.java
=eagle_sms
service/SmsSendService.java
service/SmsDeleteService.java
=eagle_state
Activity/OnePxActivity.java
service/StateService.java
Receiver/State3Receiver.java
*/e/f.java
=eagle_ui
service/CameraService.java
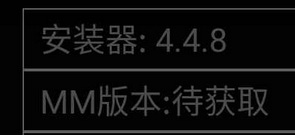
Version 4.4.8
caa93aa37353cab26a30e291c41fe579d3304e1a “SIM Card Service”
impersonating the icon of “com.android.stk”
eagle string no longer present, and the format of the code has changed, now using “GuideUtils”
Some MM Specific strings in newer versions
"屏幕下方的红色字体为操作提示,请按此提示设置MM,若未出现红色字体,请点击第一个按钮开启提示", "好的", "first_install"
"The red font at the bottom of the screen is an operation prompt. Please follow this prompt to set up MM. If the red font does not appear, please click the first button to turn on the prompt", "OK",
-
MainActivity.this.b, "若出现弹窗,请允许或确认,有不再提示的需勾选上,震动后,再次启动MM不再有弹窗"
“MainActivity.this.b, "If a pop-up window appears, please allow or confirm. If you do not want to be prompted again, you need to check it. After the vibration, there will be no pop-up window when you start MM again."
-
App.a("OpenCDB无网络,切换到能正常访问网络的WIFI,然后 再启动MM"
App.a("OpenCDB has no network, switch to WIFI that can access the network normally, and then start MM"
Button set.Text Strings
button.setText("允许SIM卡服务权限");
button.setText("允许 SIM卡服务 每一个权限");
button.setText("允许SIM卡服务每一项");
button.setText("允许SIM卡服务 自启动");
button.setText("允许SIM卡服务自启动");
button.setText("允许每一项权限");
button.setText("允许系统服务自启动");
button.setText("关闭 神隐模式");
button.setText("关闭通知栏安全提醒");
button.setText("开启SIM卡服务自启动");
button.setText("打开智能管理器");
button.setText("打开酷管家");
button.setText("打开金立系统管家");
button.setText("禁止自动清理");
button.setText("禁止通知栏耗电提醒");
button.setText("设置SIM卡服务所有权限为允许");
button.setText("设置SIM卡服务无限制");
(Google Translate)
button.setText("Allow SIM card service permissions");
button.setText("Allow SIM card service every permission");
button.setText("Allow each SIM card service");
button.setText("Allow SIM card service to start automatically");
button.setText("Allow each permission");
button.setText("Allow system services to start automatically");
button.setText("Allow each permission");
button.setText("Close invisible mode");
button.setText("Close the notification bar security reminder");
button.setText("Turn on SIM card service auto-start");
button.setText("Open Smart Manager");
button.setText("Open Cool Manager");
button.setText("Open Gionee System Manager");
button.setText("Disable automatic cleaning");
button.setText("Disable notification bar power consumption reminder");
button.setText("Set all permissions of SIM card services to allow");
button.setText("Set SIM card service to unlimited");
Interesting Strings
API
public class c {
public static Boolean a = true;
public static String b = "iloveu!jack";
public static String c = "redacted"; (this is a Wuhan #)
public static String d = "/api/user/report";
public static String e = "/api/user/report_state";
public static String f = "/api/data/report_data";
public static String g = "/api/data/report_record";
public static String h = "/api/data/report_file";
public static String i = "/api/data/report_gps";
public static String j = "/api/data/report_sms";
public static String k = "/api/data/report_calllog";
public static String l = "/api/message/response";
public static String m = "/api/data/get_config";
public static String n = "/api/data/reportKeyInput";
public static String o = "/api/data/reportSmsSend";
public static String p = "/api/data/reportSmsDelete";
public static String q = "/api/data/reportCalllogDelete";
public static String r = "data";
public static String s = "browser";
public static String t = "chat";
only present in 9 of 17 samples
“phone number”
yes, the first 2 of the 17 samples have a Wuhan number in it
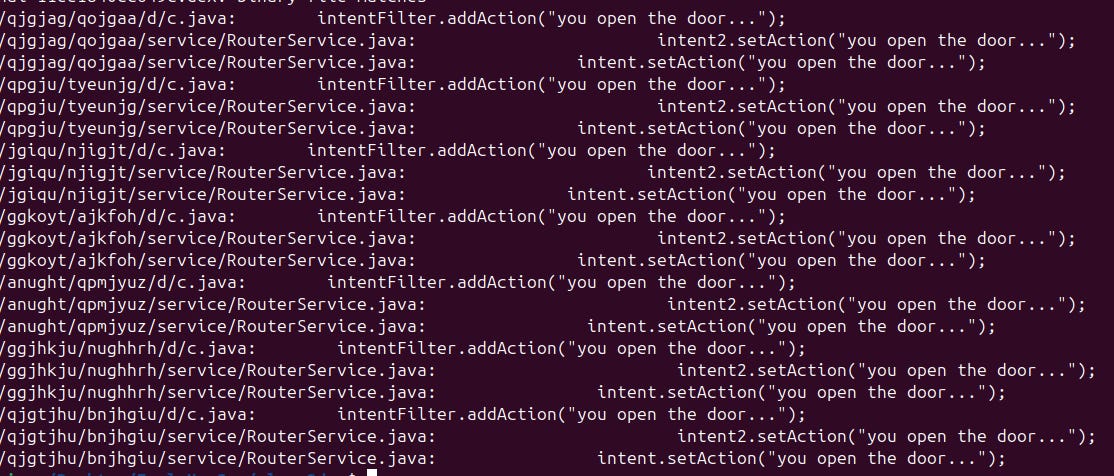
“iloveu!jack"
only present in 9 of the 17 samples
"you open the door..."
only present in 7 of the 17 samples
"手机端MM已开始激活"
(Google Translate) "Mobile MM has started to activate"
present in 9 of the 17 samples
Back to the future
SHA-1: 0b1d3d87a453f63129e73b2a32d95ef3eea94b4e
Package name: com.baidu.service
This is what one of the earliest samples of this family looked like:
Overview
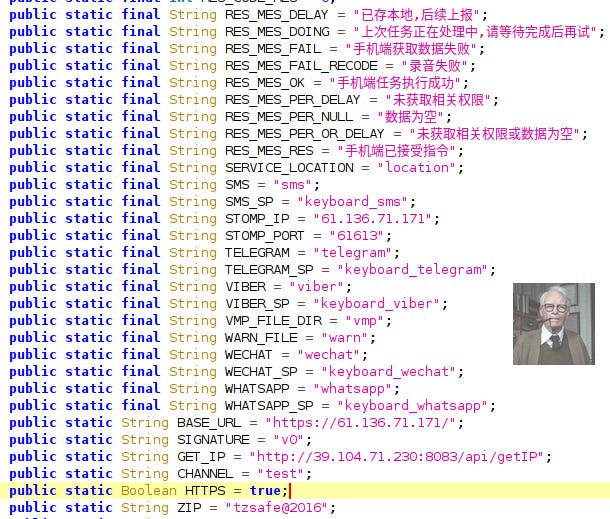
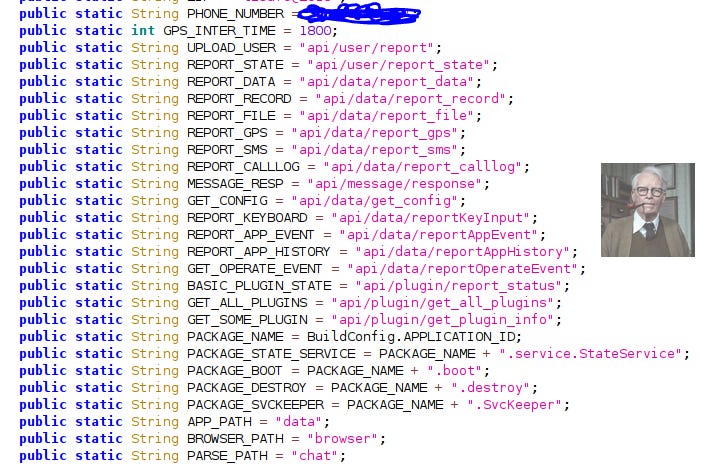
SSL Utils
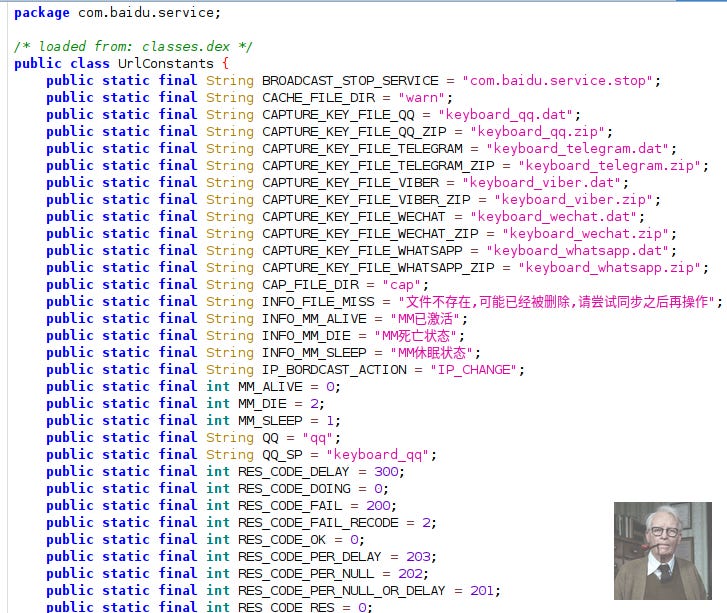
URL Constants
In true developer fashion, they gave away a lot of the goods before they figured out that they should probably encrypt and obfuscate some things…
Infrastructure pivoting
From Lookout:
61.136.71[.]171
149.28.21[.]203
47.112.137[.]199
eagle.tzsafe[.]tk
eagle.zrtsafe[.]com
i[.]tzsafe[.]com
eagle[.]tzsafe[.]com
59.48.241[.]214
61.163.69[.]238
59.48.241[.]22
220.168.203[.]197
218.200.20[.]254
202.107.80[.]34
124.163.212[.]149
119.36.193[.]210
101.201.213[.]210
www[.]tzsafe[.]com
xkong[.]tzsafe[.]com
kong[.]tzsafe[.]com
eagle[.]tzsafe[.]com
bug[.]tzsafe[.]com
qzapp[.]tzsafe[.]com
111.21.6[.]126
From my analysis [not on blog]:
47.113.93[.]219
222.222.10[.]220
222.222.75[.]82
116.116.56[.]234
39.104.71[.]230
139.9.104[.]90 [low fidelity][Huawei Public Cloud]
112.125.27[.]121
eagle[.]demo[.]tzsafe[.]com
zrtsafe[.]com
tzsafe[.]tk
reapp[.]tzsafe.tk
efence[.]demo[.]tzsafe[.]com
wifi[.]tzsafe[.]com
wxk[.]tzsafe[.]com
www[.]tzsafe[.]com
i[.]tzsafe[.]com
xkong[.]tzsafe[.]com
kong[.]tzsafe[.]com
imsi[.]tzsafe[.]com